Security Analysis of BitForge Vulnerability in GG18/GG20 Protocol
08/14/2023
By Max
I. Background
Recently, the Fireblocks cryptography research team has uncovered BitForge vulnerability in the GG18, GG20, and Lindel 17 protocols. This vulnerability allows attackers to extract the full private key from a set of MPC key shards.
Before this disclosure, the Fireblocks team had connected with Safeheron and engaged in proactive communication. Safeheron's open-source GG18/GG20 MPC protocol was implemented strictly according to the content of their papers, meaning those using this version of the open-source algorithm might be vulnerable to similar attacks. Prior to the vulnerability disclosure, Safeheron had already fixed the issues in the open-source project, with the Fireblocks team assisting in verifying the effectiveness of the patch.
The Fireblocks team published a POC using Safeheron's open-source GG18/GG20 protocol in C++ to demonstrate and help the community understand this vulnerability.
In Safeheron's commercial version, we’ve additionally incorporated the zero-knowledge proofs from CMP20/CGGMP21 into GG18 and GG20 protocols, hence they are not affected by this vulnerability.
II. Scope of Vulnerability
This article focuses on the impact of the vulnerability on GG18 and GG20. With respect to the GG18 and GG20 protocols, an attack can be stricken during the MPC signing by crafting the specific Paillier key. With several times of signing, the attacker can extract the key shards of other participants.
The impact of this vulnerability is quite extensive. Since it challenges the security assumptions of the MPC protocol, almost all popular open-source implementations of the GG18 and GG20 protocols are affected by this vulnerability.
III. Vulnerability Mechanism
How does one attack the MPC protocol? Common MPC protocols are provably secure under certain security assumptions. Therefore, attacks on MPC protocols often focus on the security assumptions they rely on. These security assumptions are like the foundation of a skyscraper. If the assumptions fail, the entire MPC protocol will be affected.
Taking GG18/GG20 as an example, these MPC protocols depend on the security of the Paillier homomorphic encryption algorithm which is designed based on the hard computational problems of composite residuosity and is a widely used homomorphic encryption algorithm that supports addition.
The core logic of the entire attack is as follows:
(1)In the KeyGen Subprotocol phase, the attacker constructs an insecure homomorphic key.
(2)During the Sign Subprotocol phase:
Using the properties of the insecure homomorphic key, the attacker constructs malicious zero-knowledge proofs, deceiving other participants to get verified;
(3)After iterating the Sign subprotocol multiple times, the attacker calculates the other participant's key shard using the Chinese Remainder Theorem.
IV. Attack Method
In this chapter, we delve into the details of the attack. In a common MPC threshold signature scheme, there are multiple participants who can attack each other using identical attack methods.
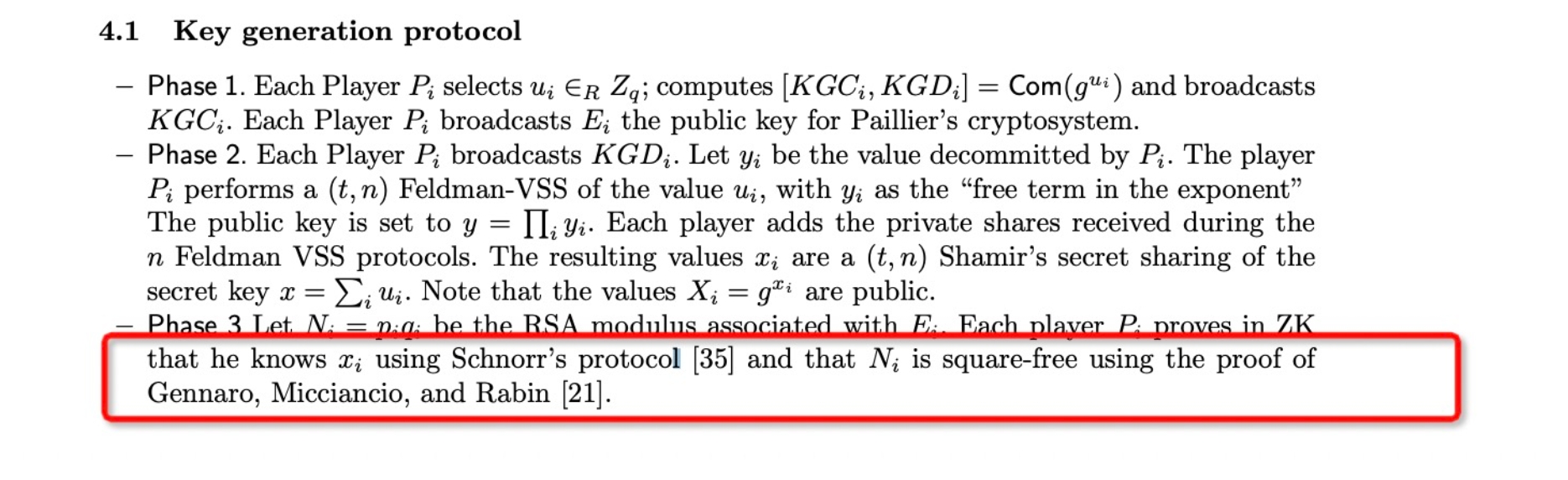
4.1 Preparation Phase: Construct an Insecure Homomorphic Key
The first attack occurs during the execution of the KeyGen subprotocol, which can be termed the "attack preparation phase". During this phase, the attacker, Party A, successfully constructs an insecure Paillier homomorphic key.
The standard process for constructing a homomorphic key is:
Compute:
The process used by Party A (attacker) to construct the homomorphic key is:
Compute:
4.2 Attack Phase: Sign Subprotocol
The standard calculation is:
Execute the MPC Sign subprotocol as usual.
The attacker's computation process is:
Create a malicious zero-knowledge proof to deceive the other party.
Execute the MPC Sign subprotocol as usual.
Here are its specific operations:
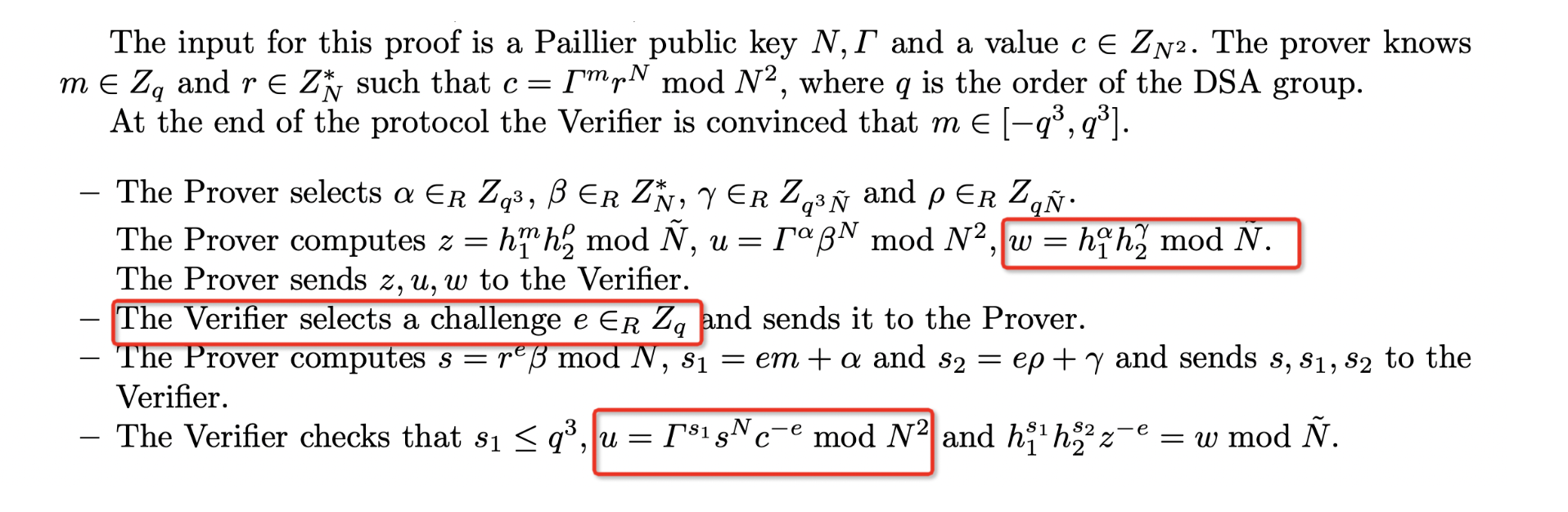
Craft a Zero-Knowledge Proof
Witness:$k_A' = 0 \ne k_A$, other random numbers.
Please note the above is an illegal statement:
Normally, the range proof of the GG18 protocol here is fully valid, making it difficult for the attacker to construct a zero-knowledge proof that allows the statement to get verified.
According to the description of zero-knowledge proof in GG18 and GG20 protocols:
In the Verifier's verification process, the most crucial aspect is ensuring the satisfaction of the equation for ciphertext constraints (highlighted in the red box):
As known:
4.3 Final Phase: Compute the Victim's Key Shard
Upon successfully executing the MPC Sign subprotocol 16 times, the attacker will obtain:
4.4 Attack Implications
The ramifications of the attack depend on the specific implementation version of the GG18 paper. Let's analyze based on the different versions:
The revised paper of GG18 offers numerous security enhancement recommendations, thus it is advisable to implement this MPC protocol based on the revised version.
V. Example Attack in Self-Custodial MPC Wallet
While the previous sections elaborated on the vulnerability’s theoretical underpinnings and algorithmic exploit method, how it plays out in a self-custodial MPC wallet? If the MPC protocol employed contains this vulnerability, how an attack exploit it?
The vulnerability impacts a t-of-n threshold, let’s take a simple example, 2 parties manage an MPC wallet, Party A and Party B. The signing threshold for this wallet is 2-of-2. The key shard for Party A is held by the user and is managed via a mobile App provided by the wallet service. Meanwhile, Party B's key shard is stored and utilized in the cloud by the wallet provider.
For a successful attack, the attacker would need:
Comprehensive understanding of the wallet provider's mechanism for wallet creation and transaction initiation.
The capability to simulate the provider's App to execute the MPC protocol for wallet creation and transaction signing.
Attack Execution (with the above capabilities):
In the described scenario, an attacker must initiate their attack right at the wallet creation phase. Subsequently, by conducting multiple signings using the wallet, the attacker can finally extract its private key.
VI. Vulnerability Remediation
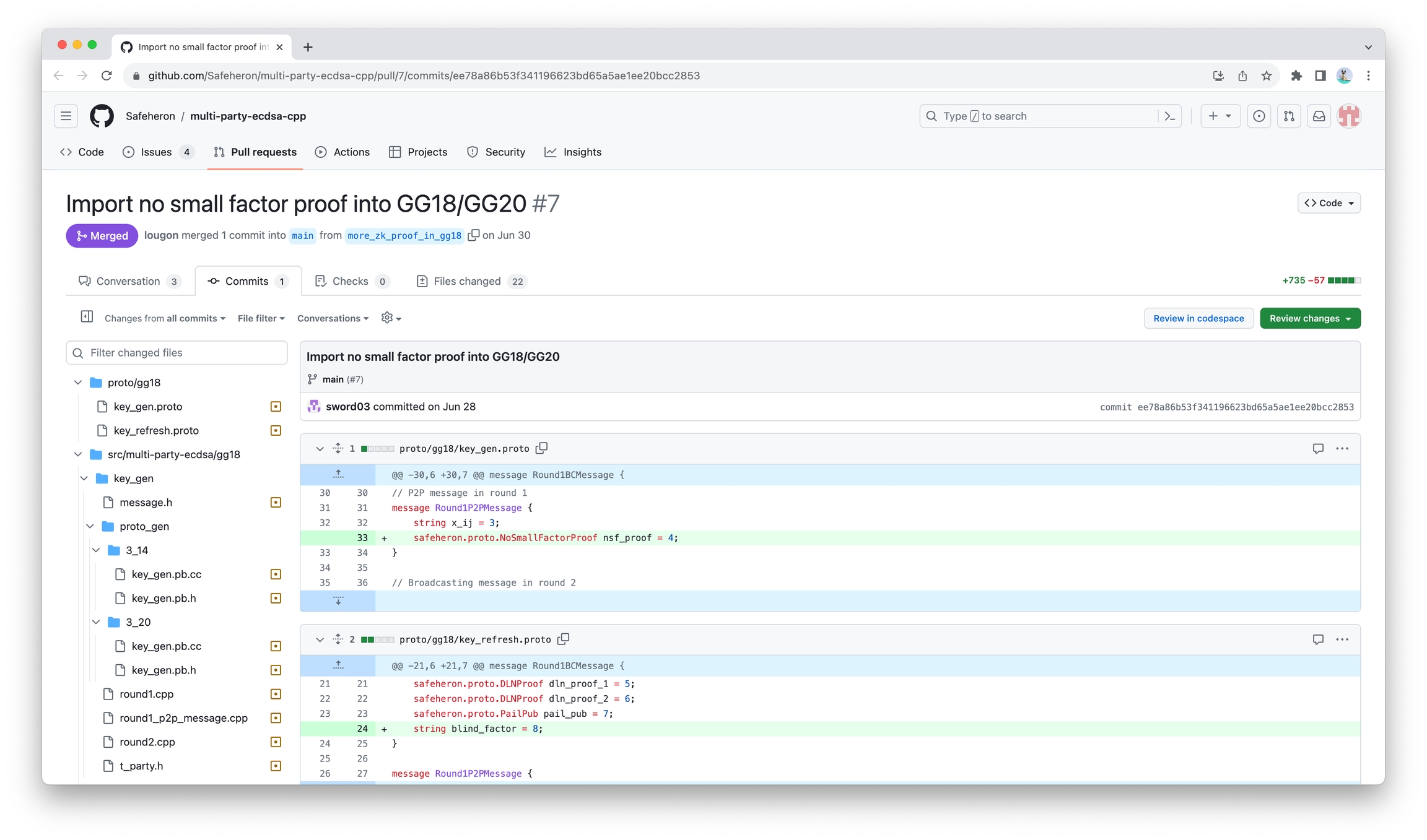
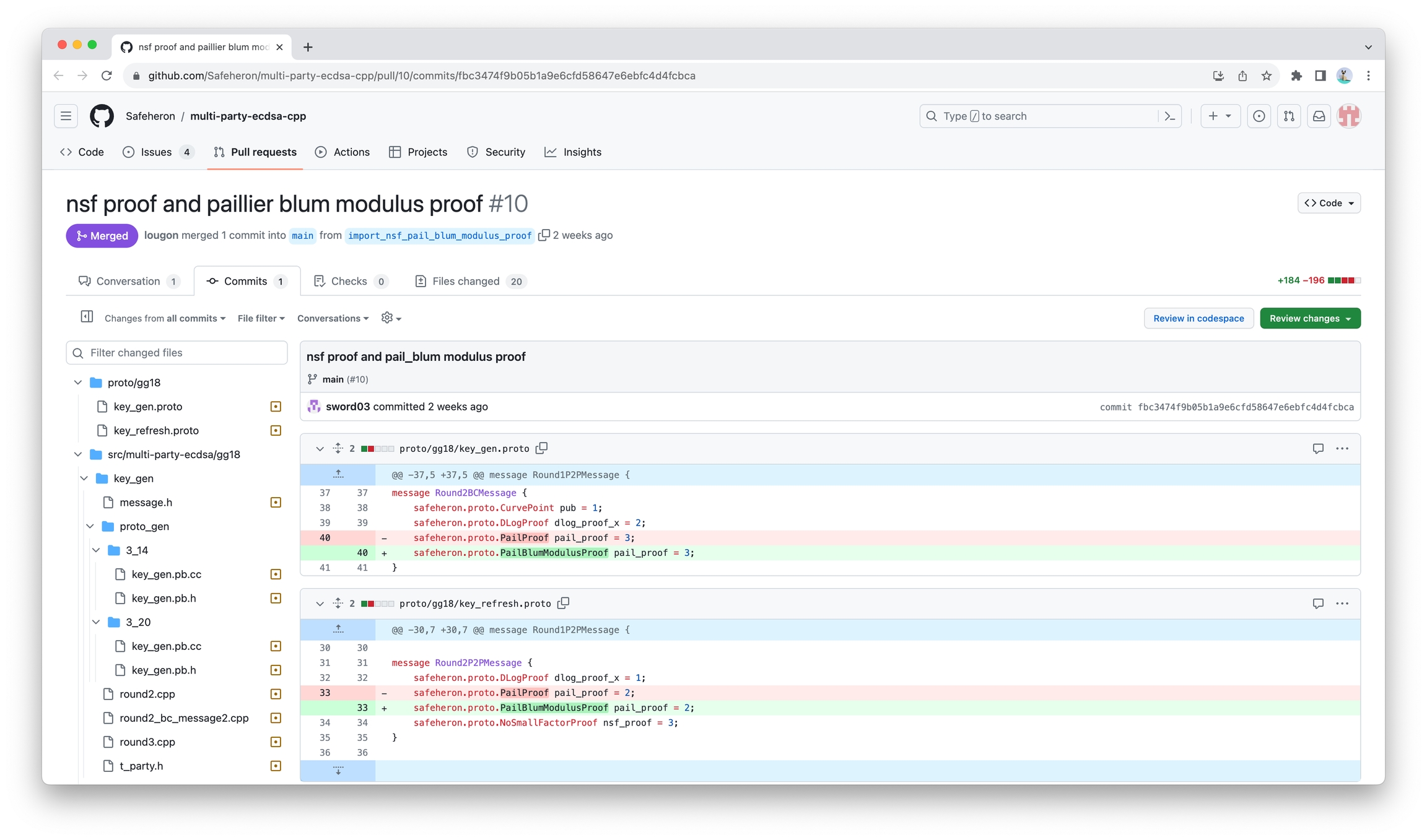
Add two zero-knowledge proofs to fix:
Safeheron has already patched this vulnerability in our open-source algorithm. For details, you can refer to:
VII. Attack Detection
Safeheron offers an integer factorization tool, which facilitates swift batch testing. And, for the algorithm of integer factorization, please refer to Large Integer Factorization Algorithm and Its Practice.
VIII. Conclusion
Having delved deep into the intricacies of this vulnerability and its exploitation method, it's evident that exploiting this loophole requires a significant level of expertise. Nonetheless, in the security industry, as we traverse the challenging dark forest filled with unknowns, we must always maintain profound respect for security.
The responsible disclosure by the Fireblocks team epitomizes that "security is never a solo endeavor." At Safeheron, we're deeply committed to the principles of open-source, transparency, and prioritizing solid technical expertise. It's indeed an honor for us to be part of this disclosure process. In the future, Safeheron will aid other industry players in patching this vulnerability with our security partner SlowMist, ensuring the safety of user assets.
Achieving industry-wide security necessitates the dedication and efforts of every tech provider, every security professional, and every user.
References
[1] Fireblocks: Practical Key-Extraction Attacks in Leading MPC Wallets
[2] GG18: Fast Multiparty Threshold ECDSA with Fast Trustless Setup
[3] GG20: One Round Threshold ECDSA with Identifiable Abort
[4] CGGMP21: UC Non-Interactive, Proactive, Threshold ECDSA with Identifiable Aborts
Last updated