Comparative Analysis of 5 Major Digital Asset Custody Solutions
08/18/2021
By Feri
The blossom of the blockchain industry attracts thousands of entrepreneurs around the world. A mass of blockchain startups have spread out over every node in the blockchain ecosystem. Also, dividends brought by speedy development charm lots of digital asset investors to join in.
Different from the traditional Internet, blockchain network focuses more on the transmission of value, that is, digital assets. As a fresh new asset type, its generation, storage, management and transmission are all distinct from the traditional ones.
I. 5 Major Digital Asset Custody Solutions
How should we have secure custody for digital assets? Entrepreneurs and investors all face this challenge. As an important field in blockchain industry, now the market has the following 5 major solutions:
1. Third-Party Custody
Third-party custody, that is to let a third party entirely manage customers’ assets. Just like banks in traditional finance and Alipay, you only need to create an account and deposit your assets into it. Then, how assets to be secured and managed will be fully up to the custodians. Besides, you won’t hold the private key for your digital assets.
Now, there are 2 major types of third-party custody in the blockchain industry, for retail investors and for institutions. For retail investors, the custody is majorly provided by exchanges, such as Huobi, Binance and Coinbase, and for institutions, generally, custody providers (custodians) will be at their service, for example, BitGo and Coinbase Custody.
Third-party custody only needs customers to create their accounts which is quite easy to start and use. This solution has always been the first choice for most digital asset investors.
But, we have to notice that once you apply third-party custody to digital assets, you will no longer hold your private key. If the custodian has some problems, you are facing the risks of asset liquidity being locked up or even lost. In February, 2014, MtGox, a major exchange accounting for 80% of Bitcoin trading volume, was hacked which incurred huge loss for many institutions and investors.
2. Single-Signature Wallet
In essence, the ownership of digital assets is the ownership of private key. Single-signature wallet is like a physical wallet for cash. Users themselves totally hold their private keys or secret recovery phrases. There are many subtypes of single-signature wallet.
According to whether it’s directly connected to the Internet, it can be divided into hot wallet and cold wallet. Or to tell from the product terminal form, there can be mobile App wallets, Web wallets, browser extension wallets, hardware wallets, etc.
There are a certain number of institutions, like exchanges and quantitative institutions, as they need frequent deposits and withdrawals from hot wallets or interactions with DeFi contracts, that they choose to store private keys on the server by themselves constructing the single-signature hot wallets on it. Nevertheless, this kind of wallet has the risks of private key leaks, single point of failure, and hacking. Every year, there are lots of hacking cases.
After DeFi Summer in 2020, lots of DeFi entrepreneurs emerged. But actually they face more risks in digital asset custody. Whether you can have secure custody over the private key of the Owner wallet concerns the life and death of a DeFi project. Quite some DeFi projects being hacked is due to the use of a single-signature wallet to manage the private key of Owner wallet.
All scenarios of digital asset custody which need to avoid single point of failure shall circumvent the use of single-signature wallet.
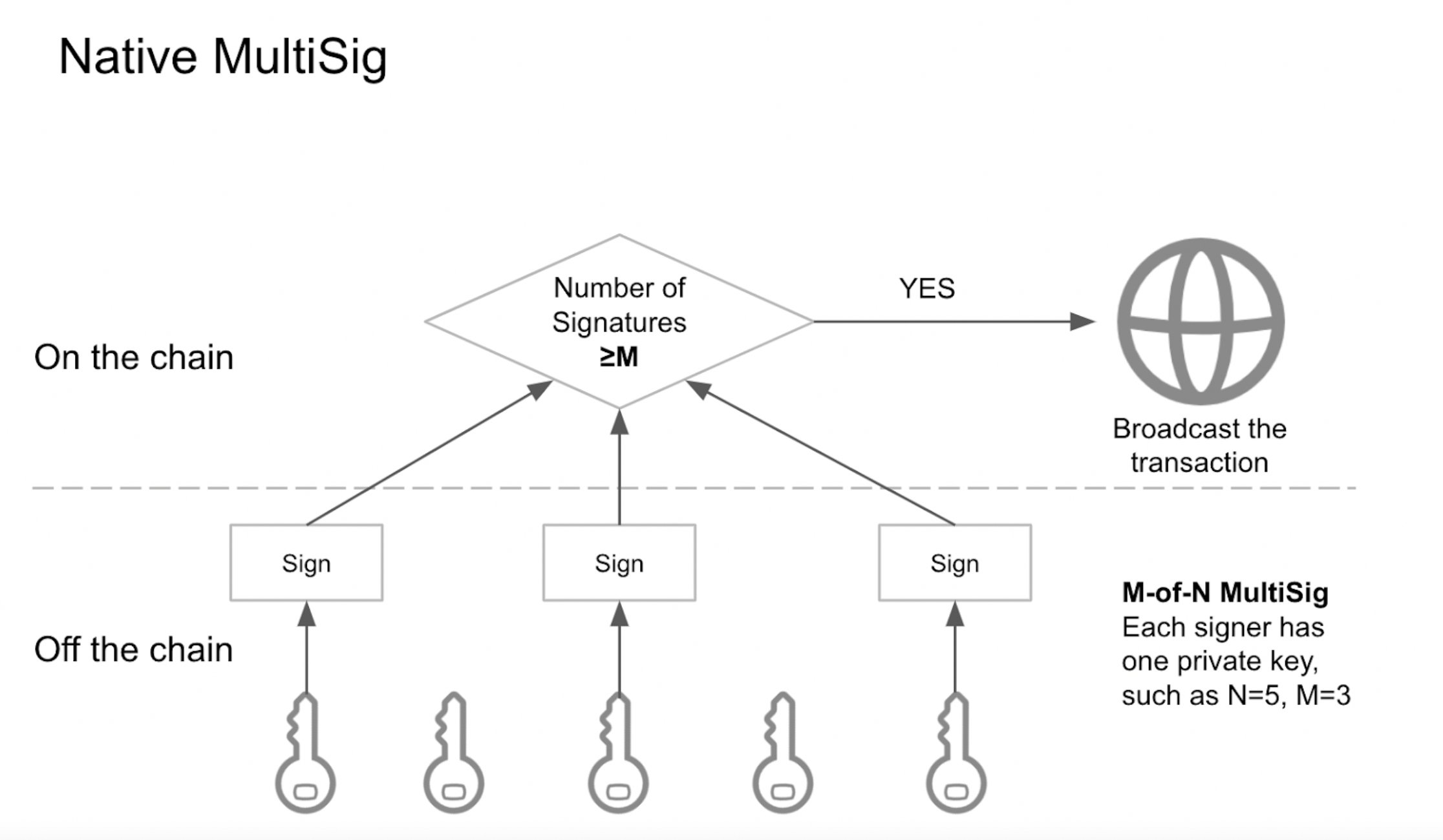
3. Native MultiSig
To solve the security risks brought by single-signature wallet, most public blockchains as Bitcoin as their representative support native multisig. Generally, multisig wallet is M-of-N wallet where N private keys jointly generate wallet address, and when a transaction is initiated, M private keys are required to sign the transaction.
Native multisig can be relatively better on avoiding the single point of failure while supporting the basic approval of asset management permissions. With these advantages, native multisig has been extensively applied in institutional-grade digital asset management.
However, native multisig has its own flaws. For instance, M-of-N mode is solidified when the wallet is created. It can never be altered. In the case of one private key being lost or leaked, the only option left is to abandon the native multisig wallet. Moreover, M signers having the same management power makes it impossible to build up a management permission hierarchy.
Meanwhile, the realization of native multisig differs among public blockchains which leads to few wallets can widely support native multisig of different public blockchains. In addition, EVM public blockchains as Ethereum being representative do not support native multisig either. These all raise the bar for the popularization of native multisig.
Native multisig also has other problems like low privacy of multisig policies, high gas fees and redundant transaction procedures.
4. Contract MultiSig
Due to Ethereum-represented EVM public blockchains do not support native multisig but support Turing-complete smart contracts, therefore, contract multisig is born. The principle is similar to native multisig, that is, generally, to deploy multisig contracts on EVM public blockchains represented by Ethereum and then generate one multisig wallet address to implement M-of-N multisig.
The emerging DeFi, NFT and GameFi ecosystems based on Ethereum-represented EVM public blockchains have a broad range of needs for smart contract Owner wallet multisig solutions.
But, akin to native multisig, contract multisig faces problems like low privacy of multisig policies, high gas fees and redundant transaction procedures too.
Besides, applying contract multisig needs to deploy smart contracts on one’s own which means the threshold is pretty high. Generally, one comparatively secure and reliable smart contract needs to be audited by a security company and the costs are also quite high.
If the quality of the deployed smart contract is not good enough, then, there are still risks of hacking. This hinders the widespread application of contract multisig as well.
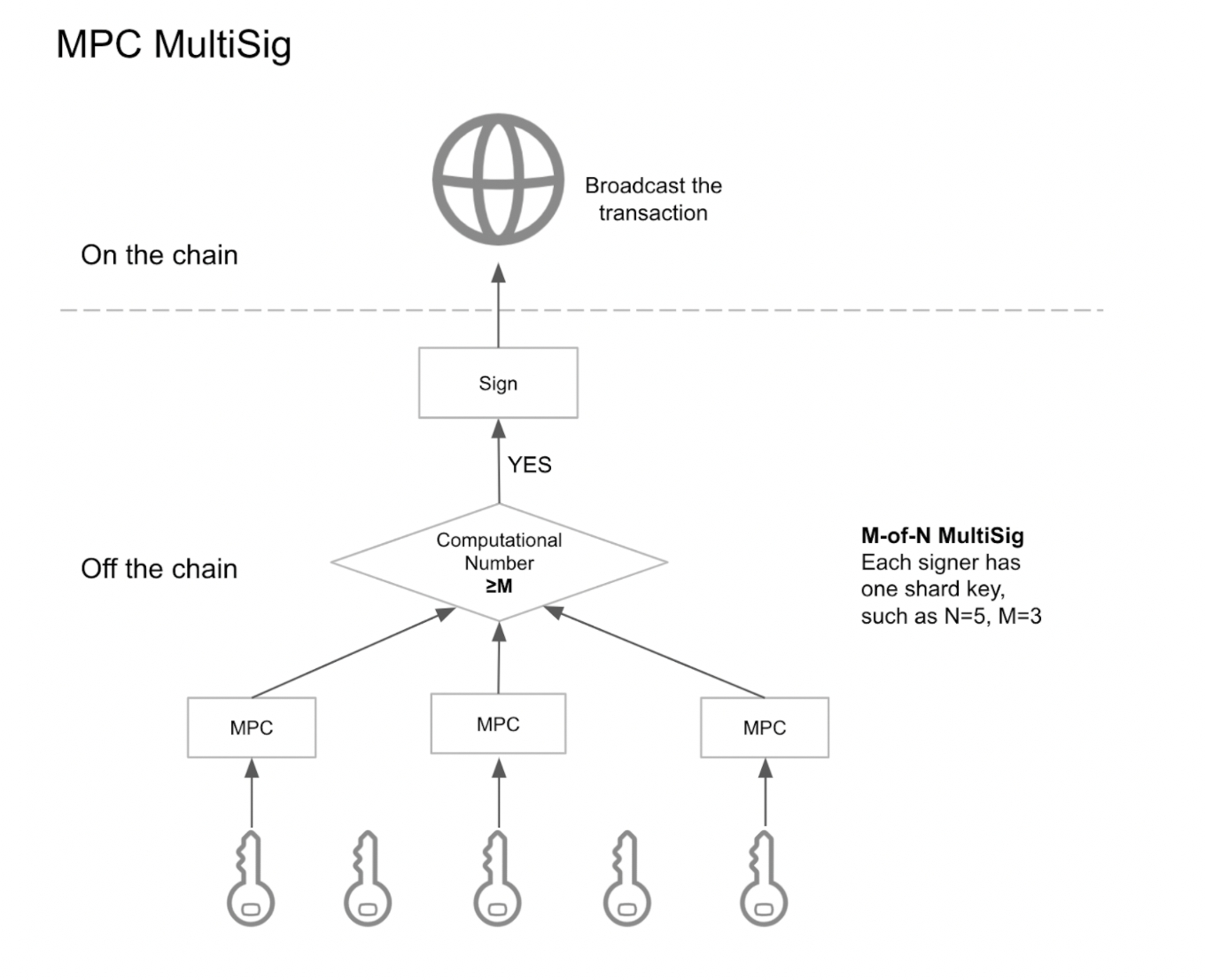
5. MPC MultiSig
Is there any solution, being safe and in a distributed manner, not only meets multisig needs, but also solve the problems of native multisig and contract multisig? Yes, we do have. MPC-based distributed threshold signature, that is MPC multisig.
*MPC: Secure Multi-Party Computation/ Multi-Party Computation
MPC multisig can realize universal multisig for common public blockchains and tokens. When sending a transaction, the MPC protocol will achieve distributed authorization. For the final step, only one on-chain signature will be needed, which largely lowers the gas fees. During the signing, the shard key will not contain any leak of plaintext bringing higher security.
Now, the commercial-grade MPC multisig solutions require relatively high-performance servers for efficient multi-party computation. The deployment costs can be at a higher level. Thus, MPC multisig suits institutions with demands for single point of failure elimination and hierarchical approval, such as exchanges, large OTC, quantitative institutions, asset managers, funds and DeFi projects.
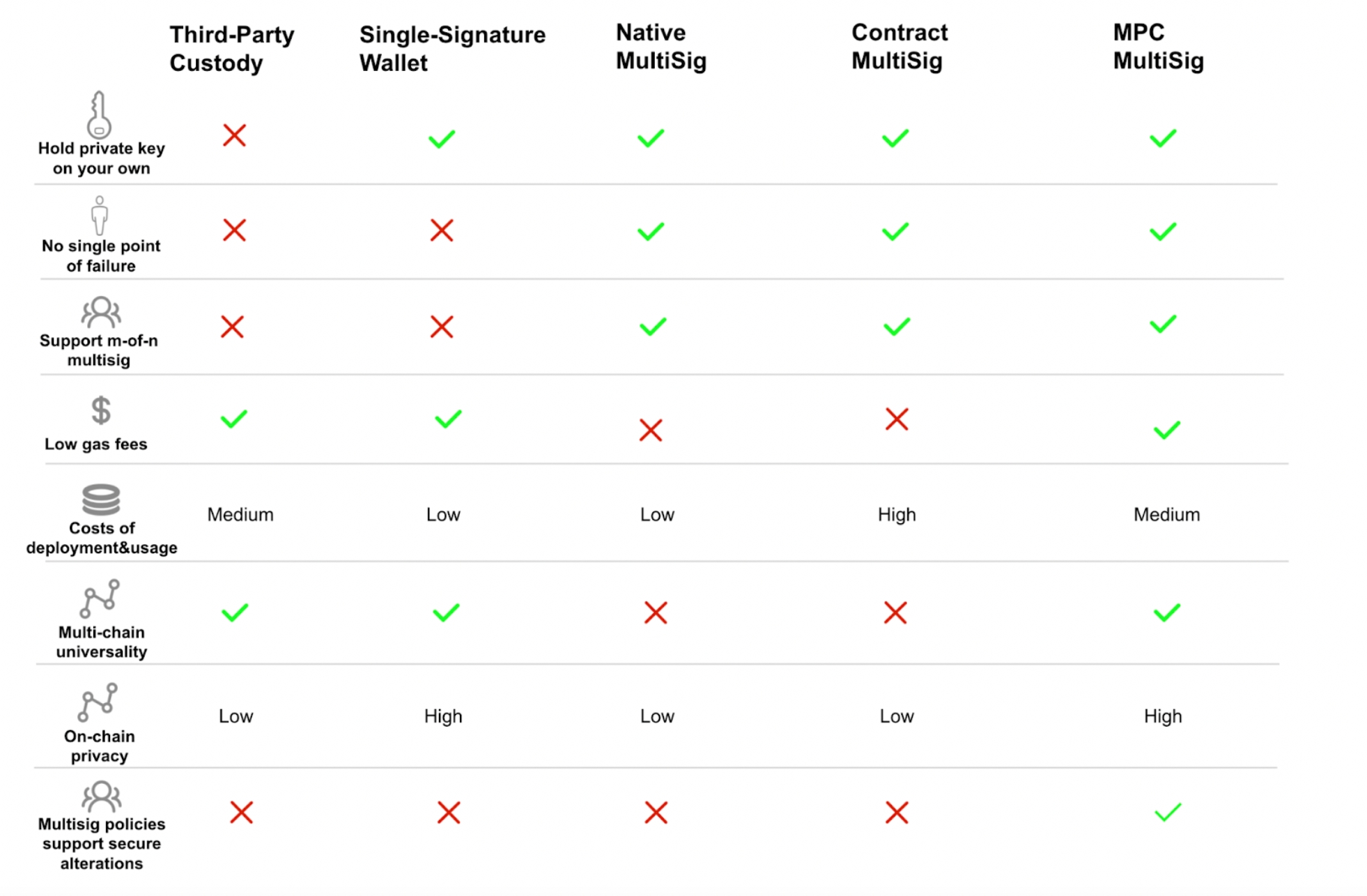
II. Comparison of 5 Solutions
We can summarize each strength and weakness of the above 5 solutions as follow:
Last updated